
CRYPTOWALL 3, a variation of CRYPTOLOCKER, is the latest in the ransomware attacks affecting business and individual networks this year. If you are infected with this malware, you will see a HELP_DECRYPT file when you login to Windows. This is a shortcut to a website with information on how to pay the ransom.
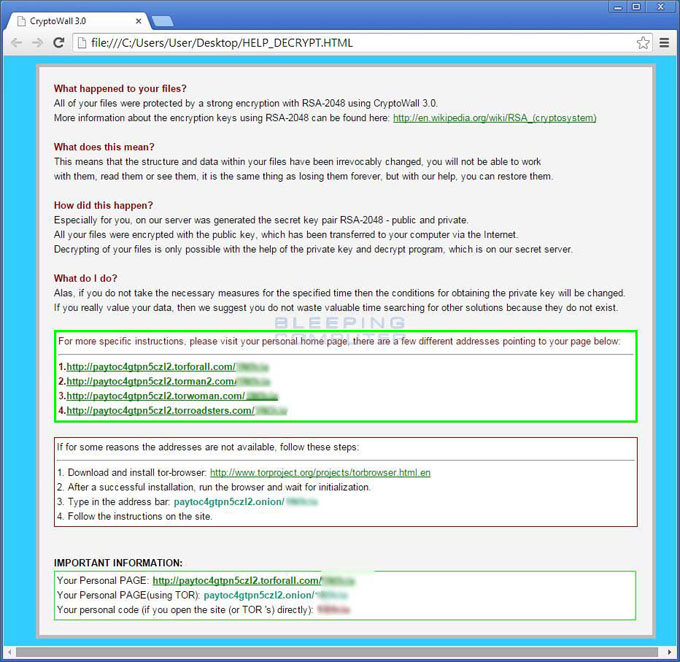
Image source: Bleeping Computer.
How does ransomware work?
The ransomware is able to gain access to your system through corrupt email attachments and malicious links. It is not detectable by your spam filter because it is able to mask itself as a legitimate file. Typically, the email will come from UPS, Dropbox, disguised as a copier scan or another seemingly reputable source. It will have a link for you to click on, allowing the ransomware to begin its work in the background.
The damage will not be noticed immediately. Once your system has been infected with ransomware, it will find user documents, images, and files, and encrypt them so you will no longer have access to those files and documents. You won’t begin to notice the effects for as long as a week after you’ve been infected.
This ransomware is not a virus, so antivirus software is virtually useless against it. It affects shared files and folders. The bulk of file and folder sharing actually comes from your server, not a local computer.
The key to avoiding an attack is to take measures to prevent one.
Stay current on all software updates. This includes Adobe Flash Player, Javascript, and Internet Explorer, which are the most common exploits used by those distributing ransomware.
Educate your employees about internet security. This will be your biggest defense against ransomware. Watch for red flags in emails you receive, and do not click them. Red flags that indicate malicious intent are usually attachments or links that end with .EXE, . ZIP, and .SCR. Dropbox, copiers, UPS, Microsoft, or any major company or service will not send an encrypted fax as an email. Also, don’t download anything, including programs, and Adobe Flash or JavaScript updates, from the internet that isn’t from a reputable source. Simply Google searching the download is not the best option, as this can bring in CRYPTOWALL.
What happens if I become infected with CRYPTOWALL 3?
Backups are crucial in order to recover from an attack like this. Antivirus software can remove the malware from your system, but it can’t restore the encrypted files. There is no way to recover your data without a backup, as paying the ransom is risky and doesn’t guarantee your data will be restored.
We currently offer 2 types of backups. File and Folder is a simple backup where you choose what files and folders are to be backed up. This will back up files and folders you choose at a set time, and sends your data to an offsite data center. If all of your data was lost, only the designated files and folders would be preserved.
The second type of backup, which is recommended, is known as an image based backup. It backs up the entire server or desktop in a specific point in time, known as an image. An image based backup preserves all of your data, so you can restore all of your information with minimal downtime in the event of a disaster.
An up-to-date system backup will help get your data back. If you would like to know more about how to protect your business from a cyber-attack, or find that your system is infected, speak to one of our IT consultants at 912.354.8900.
